Cyber threats are getting smarter every day. In 2024, businesses across the United States faced over 3,205 data breaches affecting more than 353 million people. That is not just a number on a screen. Those are real companies losing money, trust, and customers.
If you are searching for tatasec valuable resources, you are already ahead of the curve. You know that protecting your business means more than installing antivirus software and hoping for the best. You need real tools, proper training, and expert guidance to stay safe.
Tatasec valuable resources give you exactly that. They bring together everything you need in one place. From threat detection systems to employee training programs, these resources help businesses of all sizes defend against cyberattacks. Whether you run a small startup in Austin or manage IT for a healthcare company in New York, these tools work for you.
This guide breaks down the most important tatasec valuable resources. You will learn what they are, how they work, and why they matter for your business. No confusing tech jargon. Just clear, practical information you can use right away.
Key Takeaways
- Tatasec valuable resources combine security tools, training, and expert support in one ecosystem
- Real-time threat detection systems monitor your network 24/7 to catch attacks before they cause damage
- Employee training programs reduce human error, which causes 88% of all data breaches
- Compliance management tools help businesses meet regulations like HIPAA, GDPR, and PCI-DSS
- These resources work for businesses of all sizes, from small startups to large enterprises
What Are Tatasec Valuable Resources?
Tatasec valuable resources are a complete set of cybersecurity tools and services designed to protect businesses from digital threats. Think of them as your security toolkit, training academy, and expert consultant all rolled into one.
These resources cover every part of cybersecurity. They help you detect threats, train your team, manage compliance requirements, and respond to incidents. Instead of buying different tools from multiple vendors, you get everything in one integrated system.
The Tata Group backs these resources with decades of technology experience. That means you get enterprise-level security without enterprise-level complexity. The tools are built to be user-friendly, so you do not need a team of cybersecurity experts to use them effectively.
What makes tatasec valuable resources different from other security solutions? They focus on practical protection. You get real tools that solve real problems, not just fancy dashboards that look impressive but do not actually stop attacks.
A retail company in Chicago used these resources after experiencing a phishing attack that compromised customer payment information. Within three months, they had zero successful phishing attempts. Their employees learned to spot fake emails, and the automated systems blocked suspicious links before anyone could click them.
Why Do Businesses Need Tatasec Valuable Resources?
Cybercriminals do not take days off. They work around the clock, testing your defenses and looking for weak spots. Small businesses face just as many attacks as large corporations. In fact, 43% of cyberattacks target small businesses because hackers know they often have weaker security.
The average cost of a data breach in the United States reached $9.48 million in 2023. That includes lost business, legal fees, notification costs, and damage to your reputation. For many small businesses, a single major breach can force them to close permanently.
Tatasec valuable resources help you avoid becoming a statistic. They provide multiple layers of protection that work together to keep threats out. When one defense catches something, the others back it up. This approach makes it much harder for attackers to succeed.
Beyond preventing attacks, these resources help you meet legal requirements. Many industries must follow specific security standards. Healthcare providers need HIPAA compliance. Credit card processors need PCI-DSS compliance. Online businesses serving European customers need GDPR compliance. Tatasec valuable resources include tools that help you meet all these requirements without hiring expensive consultants.
A medical practice in Florida faced potential fines of $50,000 for HIPAA violations. They implemented tatasec valuable resources and passed their next audit with no violations. The compliance tracking tools showed exactly where they needed to improve, and the training modules taught their staff proper procedures.
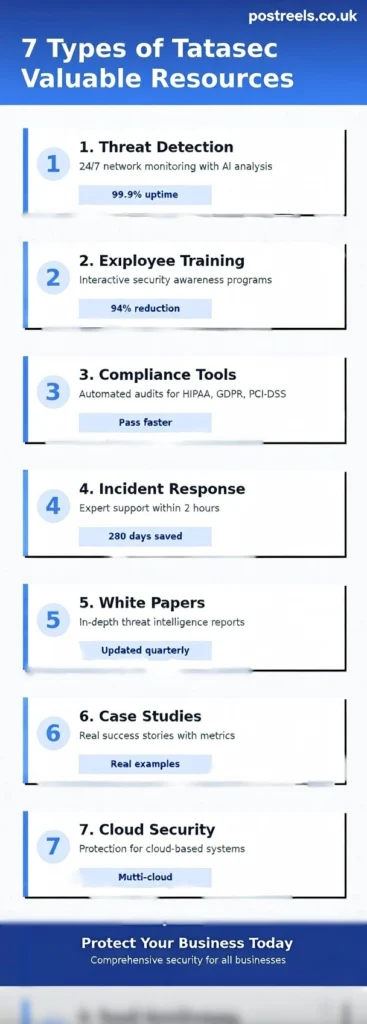
What Types of Tatasec Valuable Resources Are Available?
The tatasec valuable resources ecosystem includes seven main categories. Each category addresses a specific security need. Together, they create comprehensive protection for your entire organization.
How Do Threat Detection Systems Work?
Threat detection systems watch your network 24 hours a day, 7 days a week. They monitor every connection, every file transfer, and every login attempt. When something looks suspicious, they alert you immediately.
These systems use artificial intelligence to learn what normal activity looks like in your organization. If someone suddenly downloads 10,000 customer records at 3 AM, the system knows that is not normal. It blocks the action and sends an alert to your security team.
Real-time monitoring means threats get stopped before they cause damage. A ransomware attack can encrypt your entire network in minutes. With proper threat detection, you catch it in seconds.
An accounting firm in Boston prevented a ransomware attack that would have locked all its client files. The threat detection system identified unusual file encryption activity and automatically isolated the infected computer before the ransomware could spread.
What Makes Employee Training Programs Essential?
Your employees are both your biggest asset and your biggest vulnerability. Human error causes 88% of all data breaches. Someone clicks a bad link, uses a weak password, or accidentally sends sensitive data to the wrong person.
Tatasec valuable resources include interactive training programs that teach your team to recognize threats. The training uses real examples of phishing emails, fake websites, and social engineering tactics. Employees learn by doing, not just by reading.
The programs track completion rates and test scores. You can see which employees need additional training and which topics need more emphasis. Regular refresher courses keep security awareness fresh in everyone’s mind.
A marketing agency in Seattle reduced successful phishing attacks by 94% after implementing security awareness training. Their employees now report suspicious emails instead of clicking on them. The agency even caught several targeted attacks that bypassed their email filters.
How Do Compliance Management Tools Help Your Business?
Compliance requirements change frequently. New regulations get added. Existing rules get updated. Keeping track of everything takes serious effort.
Compliance management tools automate this process. They maintain checklists for different regulations. They schedule regular audits. They generate reports showing your compliance status. When regulations change, the tools update automatically.
These tools also help you prepare for official audits. You can run practice audits anytime. The system identifies gaps and suggests fixes. By the time auditors arrive, you know exactly where you stand.
A financial services company in Dallas used these tools to prepare for a PCI-DSS audit. They found and fixed 23 compliance issues before the auditors showed up. The audit passed without a single finding, saving them from potential fines and the cost of a follow-up audit.
What Does Incident Response Support Include?
Even with perfect security, incidents can happen. When they do, speed matters. Every minute counts when you are dealing with an active breach.
Incident response support gives you immediate access to cybersecurity experts. You get step-by-step guidance on containing the threat, removing the attacker, and recovering your systems. The support team has handled thousands of incidents and knows exactly what to do.
Response support includes forensic analysis to find out how the attack happened. You learn where your defenses failed and how to prevent similar attacks in the future. Every incident becomes a learning opportunity.
When a manufacturing company in Detroit discovered unauthorized access to their production systems, incident response support helped them contain the breach within 2 hours. Average containment time for similar breaches is 280 days. Quick action prevented the attackers from stealing intellectual property worth millions.
How Can Small Businesses Benefit from Tatasec Valuable Resources?
Many small business owners think enterprise security is too expensive or too complicated for them. That is exactly what hackers count on. They specifically target small businesses because they expect weaker defenses.
Tatasec valuable resources scale to fit your needs. You do not need to implement everything at once. Start with the basics like threat detection and employee training. Add more tools as your business grows.
The pricing model works for small budgets. You pay for what you use. No massive upfront investment. No long-term contracts that lock you in. If your needs change, your resources can change too.
Small businesses also benefit from simplified management. You do not need a dedicated IT security team. The systems handle most tasks automatically. When you need help, support is available through phone, email, or chat.
A family-owned restaurant chain with 8 locations in California implemented basic tatasec valuable resources for less than $500 per month. They protect customer payment data, meet PCI-DSS requirements, and train all employees on security best practices. Before implementation, they paid $2,000 for a compliance consultant who only provided a report. Now they have ongoing protection and support.
What Do White Papers and Case Studies Offer?
Knowledge is power in cybersecurity. The more you understand about threats and defenses, the better decisions you make. Tatasec valuable resources include extensive educational content that helps you stay informed.
White papers cover specific security topics in depth. You can read about emerging threats, new attack techniques, and defense strategies. The papers are written by security professionals who deal with real attacks every day.
Case studies show how other businesses solved their security challenges. You see real examples with specific results. A case study might explain how a company reduced its incident response time from 12 hours to 15 minutes. You learn what they did and how you can do the same.
These resources help you make informed decisions about your security strategy. Instead of guessing what might work, you see what actually worked for similar businesses. This saves time and money on trial and error.
How Do You Access Tatasec Valuable Resources?
Getting started with tatasec valuable resources follows a straightforward process. The entire setup typically takes less than a week, depending on your organization’s size.
First, you assess your current security situation. What protections do you already have? Where are the gaps? What regulations apply to your industry? This assessment helps determine which resources you need most urgently.
Next, you create an account and select your resource package. You can customize the package based on your specific needs. Need more training tools? Add them. Need advanced threat detection? Include that too.
Implementation support helps you get everything running smoothly. Technical experts guide you through installation and configuration. They help integrate the tools with your existing systems. They train your team on how to use everything effectively.
After setup, you get continuous support. Questions get answered quickly. Updates install automatically. Your security improves over time as the systems learn your organization and adapt to new threats.
What Makes Tatasec Valuable Resources Different from Other Solutions?
The cybersecurity market is crowded with options. Dozens of companies offer security tools. What makes tatasec valuable resources stand out from the competition?
Integration is the biggest differentiator. Most security vendors sell individual products. You buy a firewall from one company, antivirus from another, and training from a third. Getting everything to work together becomes a major headache.
Tatasec valuable resources work as a unified system. The threat detection tools share information with the incident response team. Training results feed into compliance reports. Everything connects, giving you complete visibility across your entire security posture.
The Tata Group’s reputation adds credibility. This is not a startup that might disappear next year. Tata has operated for over 150 years across multiple industries. They understand business challenges and build solutions that actually work in the real world.
Practical functionality matters more than flashy features. The tools focus on preventing breaches, not just detecting them. You get protection that works, not just reports that tell you something went wrong after the damage is done.
Can Tatasec Valuable Resources Protect Against Ransomware?
Ransomware attacks increased by 92% in 2023. Attackers encrypt your files and demand payment to unlock them. Even if you pay, there is no guarantee you will get your data back. Many victims pay the ransom and still lose everything.
Tatasec valuable resources include multiple defenses against ransomware. Email filtering blocks malicious attachments before they reach your inbox. Employee training teaches people to recognize ransomware delivery methods. Threat detection systems identify encryption activity and stop it immediately.
Backup systems provide another layer of protection. Regular automated backups mean you can restore your data without paying criminals. The backups are isolated from your main network, so ransomware cannot encrypt them.
Incident response support helps if an attack gets through. Experts guide you through containment and recovery. They help you notify customers if required. They work with law enforcement when appropriate.
A law firm in Phoenix faced a ransomware attack that encrypted 75% of its files. Because they had proper backups and a rapid incident response, they were fully operational within 6 hours. They did not pay the ransom. They did not lose a single billable hour. Total recovery cost was under $5,000, compared to the $50,000 ransom demand.
How Often Should You Update Your Security Resources?
Cybersecurity is not a one-time project. Threats evolve constantly. Attackers develop new techniques. Software vulnerabilities get discovered. Your security must evolve, too.
Tatasec valuable resources update automatically. You do not need to manually download patches or install updates. The systems handle this in the background without disrupting your operations.
Threat intelligence feeds update continuously. When security researchers discover a new attack method, the information reaches your systems within hours. Your defenses adapt before the attacks become widespread.
Training content gets refreshed quarterly. New phishing examples, updated best practices, and current threat information keep your team informed. Employees can review past modules anytime they need a refresher.
Regular security reviews help you stay ahead of threats. Schedule monthly check-ins to review your security posture. Look at incident reports. Check compliance status. Adjust your resources as your business needs change.
Tatasec Valuable Resources Comparison
Understanding the different resource types helps you choose what your business needs. This comparison shows the key features and benefits of each resource category.
| Resource Type | Primary Benefits | Best For |
| Threat Detection | Real-time monitoring, AI-powered analysis, automatic blocking | Businesses handling sensitive data, high-value targets |
| Employee Training | Automated audits, regulation tracking, and report generation | Organizations with many employees, remote workforces |
| Compliance Tools | Regulated industries like healthcare, finance, and retail | Regulated industries like healthcare, finance, retail |
| Incident Response | Expert support, rapid containment, forensic analysis | All businesses, especially those without dedicated security teams |
Frequently Asked Questions
Are tatasec valuable resources suitable for startups?
Yes, tatasec valuable resources work perfectly for startups. The flexible pricing and scalable features mean you only pay for what you need. You can start with basic protection and add more resources as your company grows. Many startups actually have more to lose from a breach because they have less cushion to absorb the costs.
How much do tatasec valuable resources cost?
Pricing varies based on your company size and which resources you need. Small businesses typically spend between $300 to $1,500 per month. Mid-size companies might spend $2,000 to $5,000 monthly. Enterprise organizations have custom pricing. Contact Tatasec for a specific quote based on your requirements.
Can I try tatasec valuable resources before committing?
Most tatasec valuable resources offer trial periods or demos. You can test the systems in your environment before making a purchase decision. This helps you verify that the tools meet your needs and work with your existing infrastructure.
Do I need technical expertise to use these resources?
No, tatasec valuable resources are designed for ease of use. The interfaces are intuitive. Setup wizards guide you through configuration. Support teams help with technical questions. While having IT knowledge helps, it is not required to use the basic features effectively.
How quickly can I implement tatasec valuable resources?
Basic implementation takes 1 to 3 days for small businesses. Larger organizations with complex networks might need 1 to 2 weeks. The timeline depends on how many systems you need to protect and whether you want custom configurations. Emergency implementations can happen faster when necessary.
What happens if I experience a breach despite using these resources?
Incident response support activates immediately. Security experts help contain the breach, remove the attacker, and restore your systems. They also conduct forensic analysis to prevent future attacks. While no security is 100% perfect, tatasec valuable resources significantly reduce both the likelihood and impact of breaches.
Will these resources slow down my network?
Modern security tools are designed for minimal performance impact. The threat detection systems work in the background without affecting your normal operations. Most users notice no difference in network speed or system performance after implementation.
Conclusion
Cybersecurity threats are not going away. They are getting more sophisticated and more frequent. Waiting until after an attack to improve your security is like buying insurance after your house burns down.
Tatasec valuable resources give you comprehensive protection without overwhelming complexity. You get enterprise-level security that works for businesses of any size. The integrated approach means all your security tools work together instead of creating gaps that attackers can exploit.
The real value comes from peace of mind. You can focus on running your business instead of worrying about the next breach. Your customers trust you with their data. Your employees depend on your systems. Tatasec valuable resources help you protect both.
Start with a security assessment. Identify your biggest risks. Choose the resources that address those risks first. Then expand your protection over time. Every step you take makes your organization more secure.
Remember, the cost of prevention is always less than the cost of recovery. Invest in tatasec valuable resources today, before you become another data breach statistic.